¶ What is the Diri Risk Analysis?
The Diri risk analysis (DRA) is the model for identifying and assessing cyber risk in the Diri software. The purpose of the DRA is to identify unacceptable cyber risks such that we can implement risk mitigating treatments. DRA is step 3 of the Diri risk assessment process. The DRA model is a combination of well-established risk science concepts and modern software functionality. Best practice information security (ISO/IEC 27005) defines the risk scenario as a combination of assets, vulnerability, threat, controls, and outcomes. In the DRA, we have expanded these concepts with our prior research findings in combination with the commonly known Bowtie risk analysis to produce a novel ISRA method and model. The software allows for many-to-many relationships between all components in the analysis.
The traditional Bowtie analysis consists of an adverse event, coupled with possible causes and outcomes of said event. The security controls in the bowtie are in place to either mitigate the cause (probability) or the outcome (consequence). The flexibility of the bowtie coupled with the Diri assessment methods makes the DRA state-of-the-art.
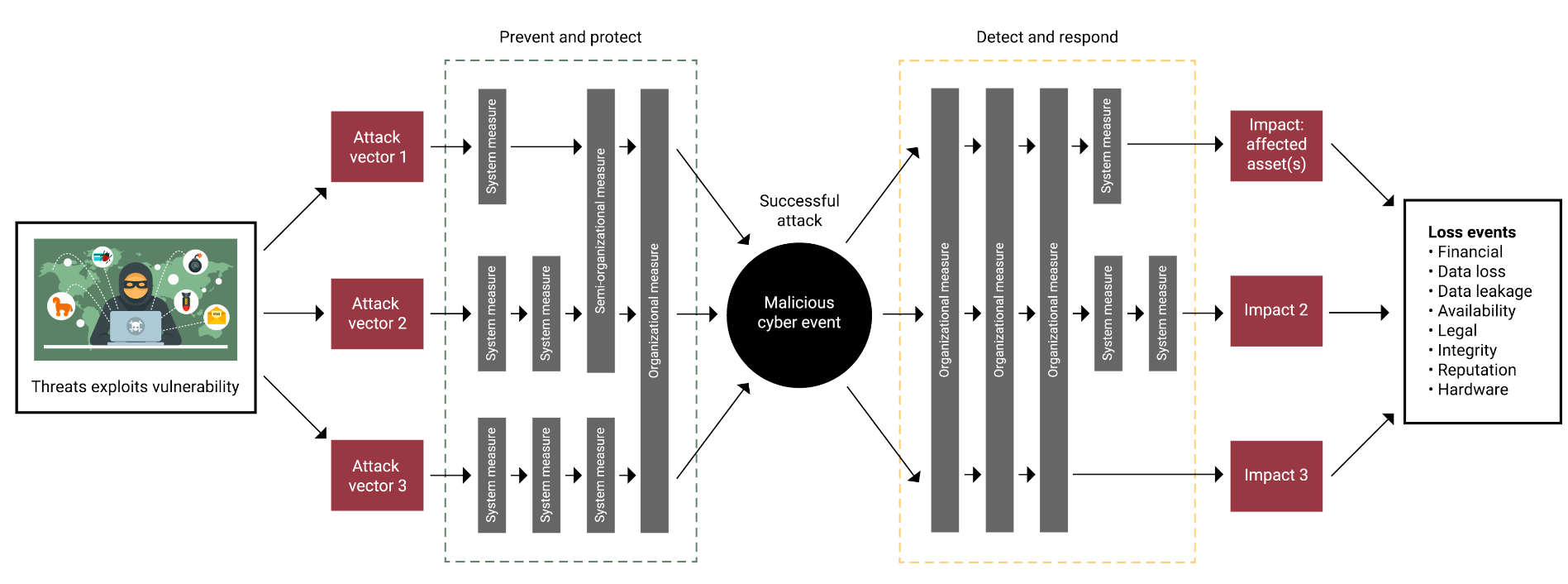
When you enter step 3 in Diri, you will meet an empty risk assessment with three main paths to start working: Causes, Events, and Consequences. The rationale behind the model is illustrated well in the picture of the DRA above.
¶ Diri risk assessment basics
The starting point for a DRA is illustrated below.
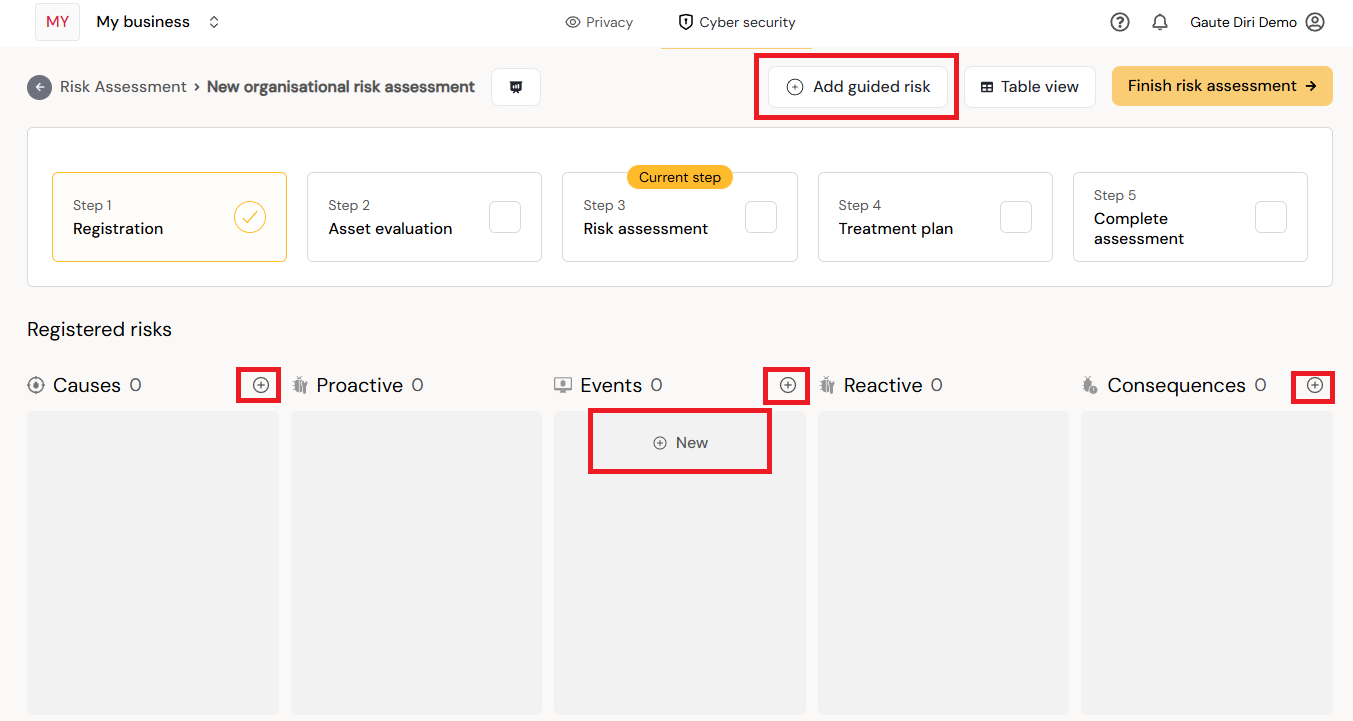
The above picture illustrates the work surface with possible interactions. The plus signs allows you add either causes, events, or consequences. Below is a short animation showing some basic features in Diri for adding new, highlighting, linking, unlinking, and adding treatments.
¶ Many-to-many relationships in the DRA
A cause can lead to several events and an event can lead to many consequences. The DRA allows you to quickly create multiple connections between these elements. Use drag and drop on the cause and consequence cards to events. How to add an existing treatment to multiple causes and consequences is described above. There are primarily two ways of connecting elements in Diri:
¶ Drag and drop
You can drag and drop causes and consequences and connect them to existing events. Grab the card cause or consequence card itself and drop it onto the event that you want to connect, as illustrated in the figure below. The chain icon bottom left on the card displays how many connections the item has to events.
¶ The “Pin Event Card” feature for large risk assessments
As the amount of causes and consequences increases, it gets harder to drag and drop causes/consequences to events. Use the Pin-feature on the event to keep the event in-screen while scrolling downwards. You can pin multiple events at once such that they are attached visible when scrolling in the work surface and allowing for drag-and-drop. The below animation shows how to pin events, scroll downwards, and drag-and-drop:

Unlinking can be done on either the cause, event, or consequence card.
¶ Editing and removing connections between elements
You have to access cause or consequence directly to remove connections between events and causes/consequences. The connections are visible in the "Linked events"-field for causes/Consequences and in the llinked field for the events. Open linked menu and click the "unlink" symbol to remove the connection or click the space behind the last event to add existing ones. The basic mechanics are illustrated below:
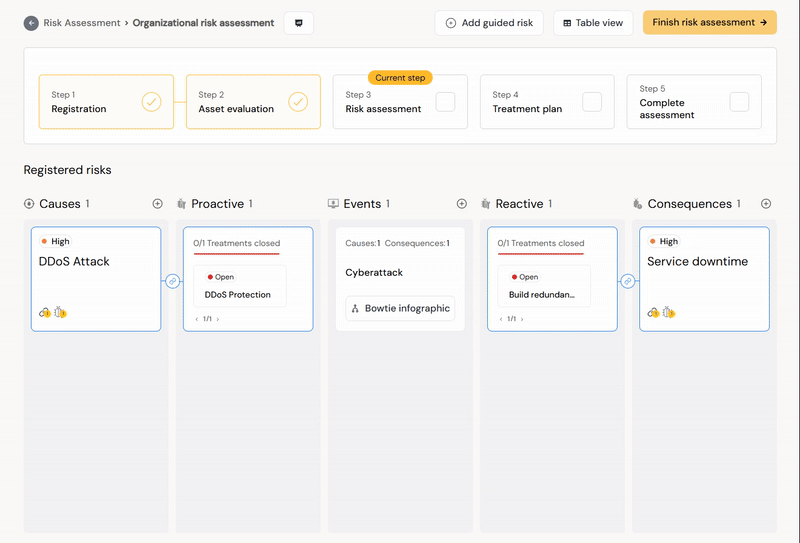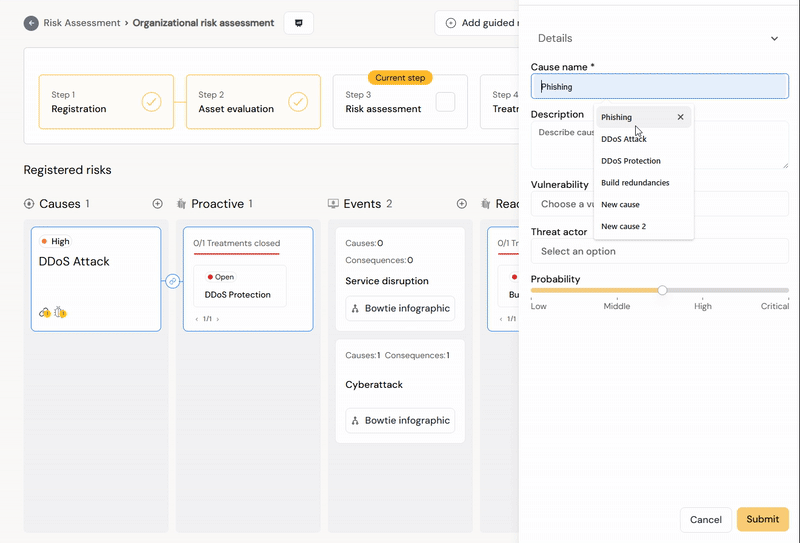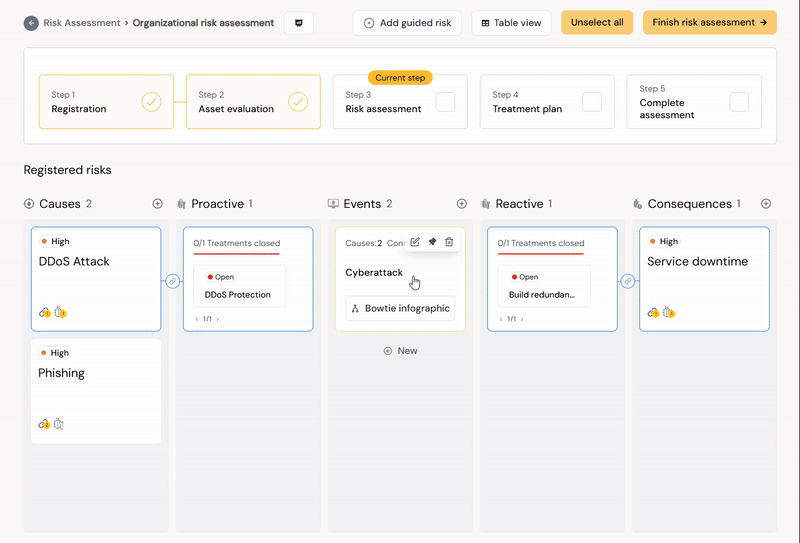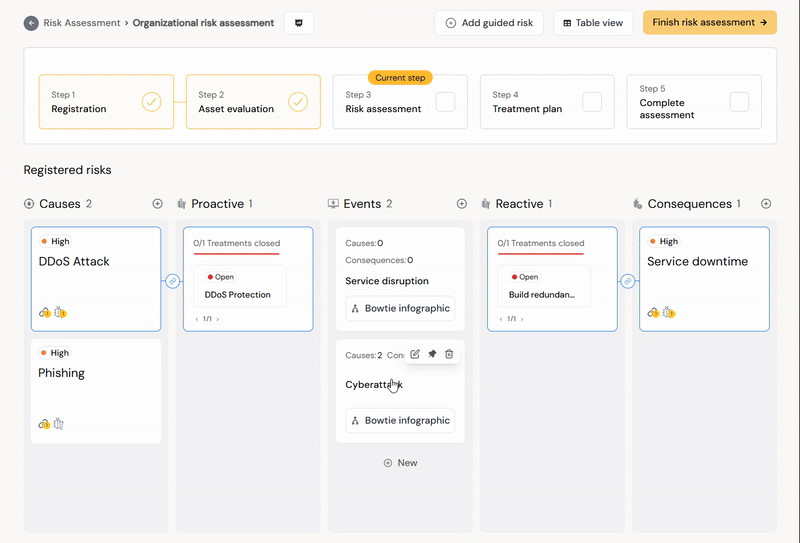
Clicking the event card will show only the event and attached items. Click the card again or unselect all button to go back to seeing all the information. Having highlighted an event means that all new causes and consequences will be linked to the event. Adding a cause or consequence to the risk assessment without having an event highlighted will leave the cause unlinked and not a part of the risk register or matrix.
¶ Risks and the risk matrix
The Diri Risk Assessment worksurface uses buttons and drag-and-drop features to enable the risk analysis. You have the possibility to visualize the bowtie using the “View infographic”-button. For a risk to show up in the risk matrix and risk register, it must be a linked cause, event, and consequence. A cause follows the probability axis of the risk matrix, and the consequence follows the impact axis.
The two above risks will be on the same axis for impact (x-axis) separated on probability (y-axis) in the risk matrix:
¶ The “Add guided risk” option
If are new to this way of working, try the “Add guided risk” feature on the top to get a step by step guide to building a bowtie. Clicking this button will take you through a linear process for creating a risk based on the cause, event, consequence way of thinking.
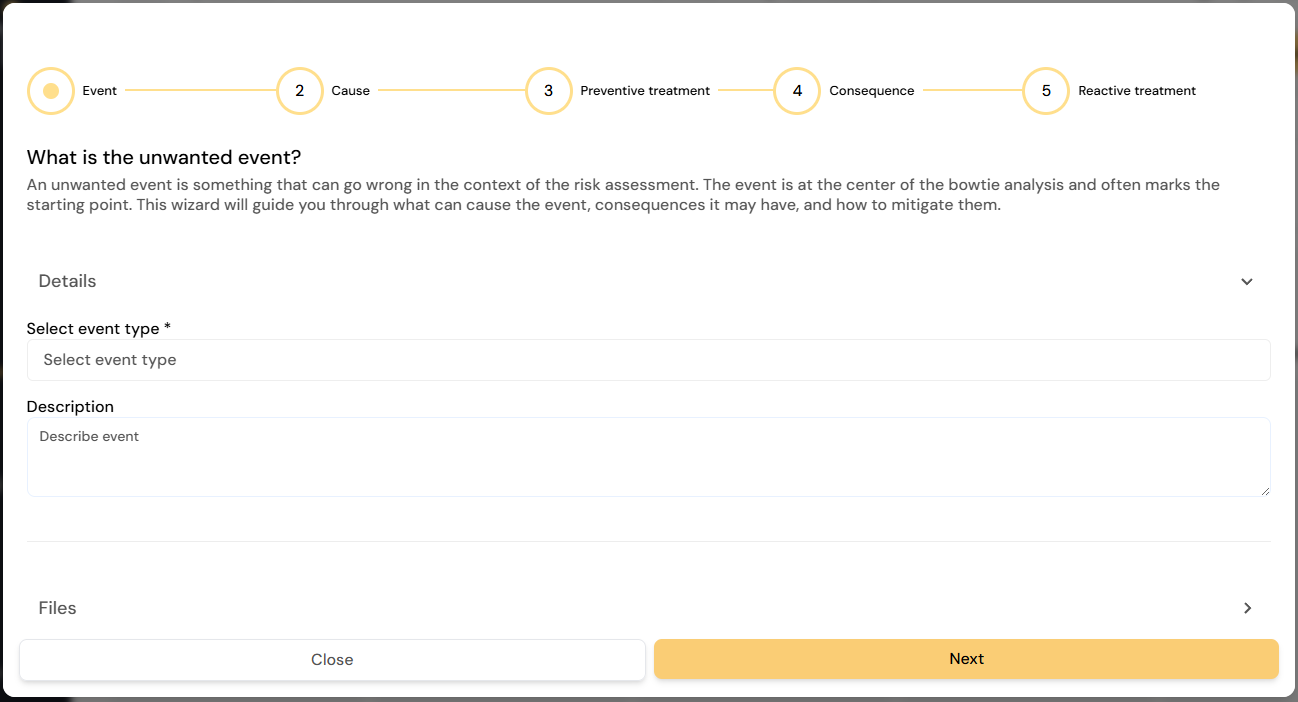
A simple guided risk walkthrough can end in a model as the one below:
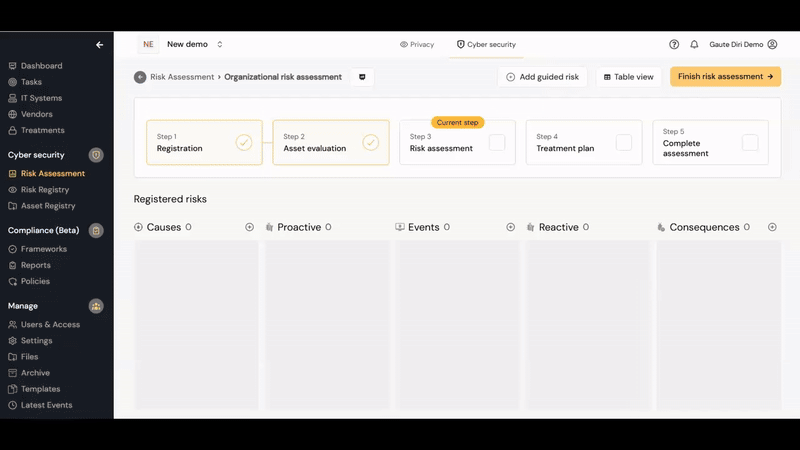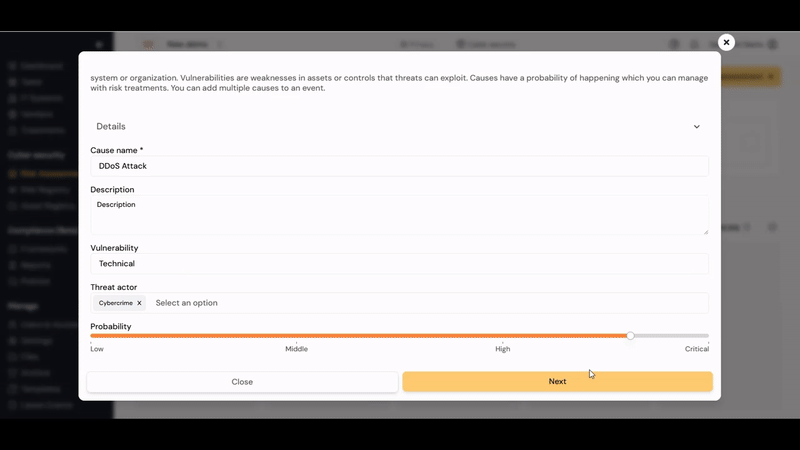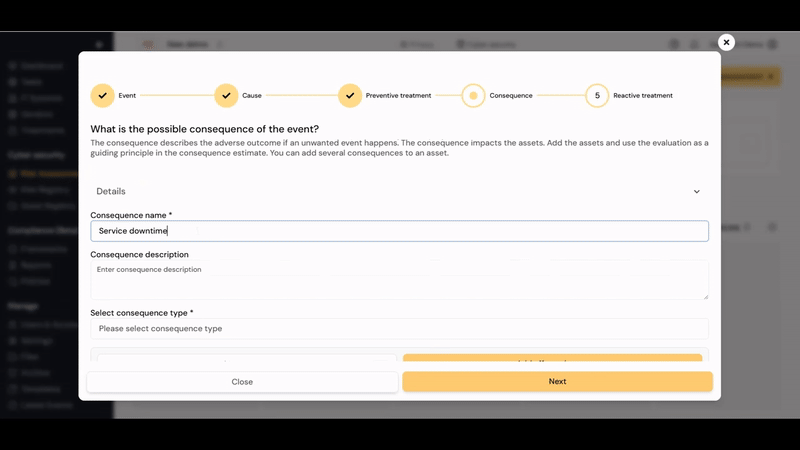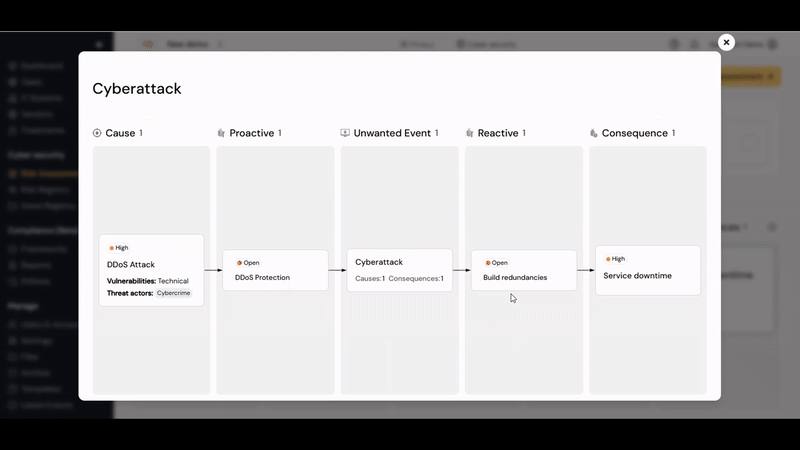
The result of the above process can be iillustrated using the Bowtie infographic:
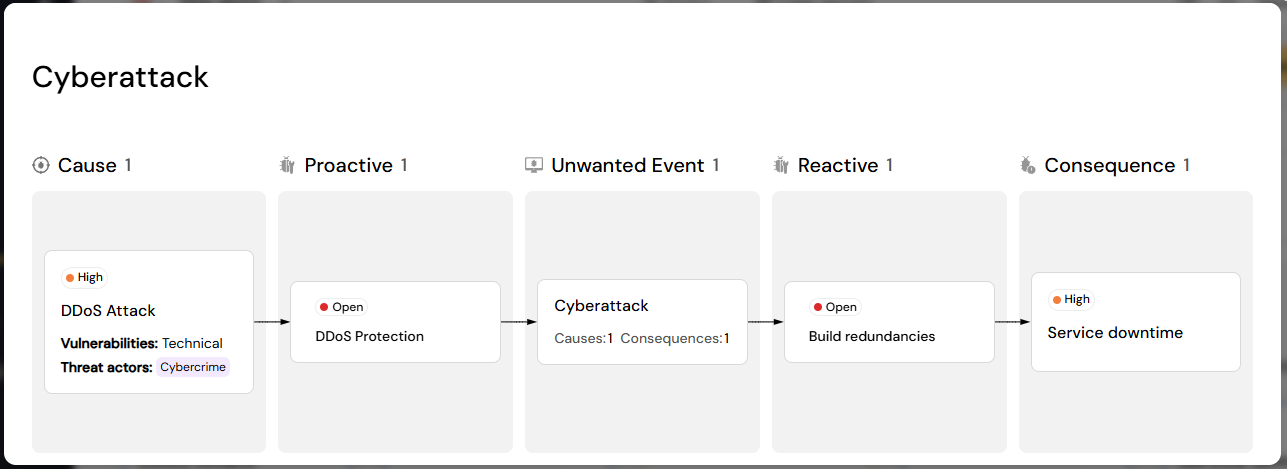
¶ DRA components
Firstly, in Diri we apply the following definitions (based on ISO/IEC 27000), starting from the left side of the risk assessment (above picture). Clicking "New" under causes will ask you to register a new cause:
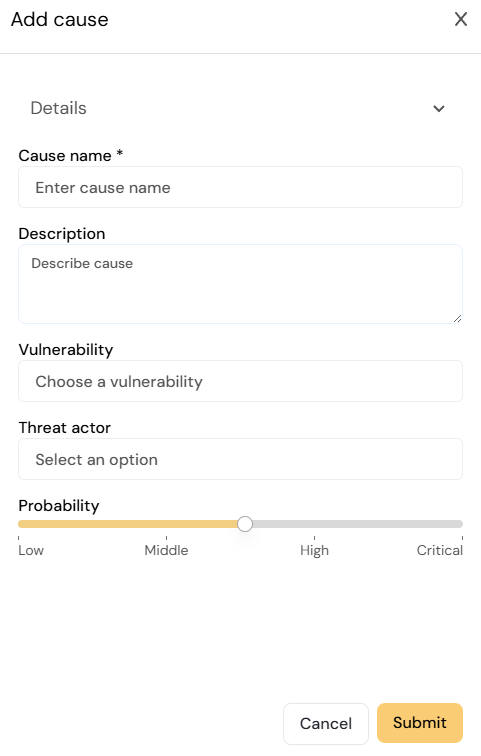
¶ Cause
- Cause: A threat exploits a vulnerability to define the attack vector (cause), leading to the event.
- Threat: The potential cause of an unwante incident, which can result in harm to a system or organization. In Diri, we focus on the person or group posing the threat, the threat actor/agent. The cause is a description of the attackers method. Diri comes with a pre-defined set of threat agents that you can add to your analysis.
- Vulnerability: Weakness of an asset of control that can be exploited by one or more threats. In Diri, we aim to quantify vulnerability using pre-defined vulnerability categories, we propose the following four categorizations, but you are free to define your own:
- Human: The attack targets and exploits human weaknesses, such as through social engineering attacks.
- Organisational: The attack targets and exploits organisational weaknesses, such as lack of oversight and control.
- Physical: The attack exploits missing physical security barriers, such as missing door locks and poor locking routines.
- Technical: The attack exploits missing or weak technical security controls, such as an exposed attack surface, outdated services or through a poorly configured firewall.
- Probability: What is the inherent probability of the threat successfully exploiting the vulnerability without considering existing controls? Both existing and new mitigating controls are added later.
¶ Event
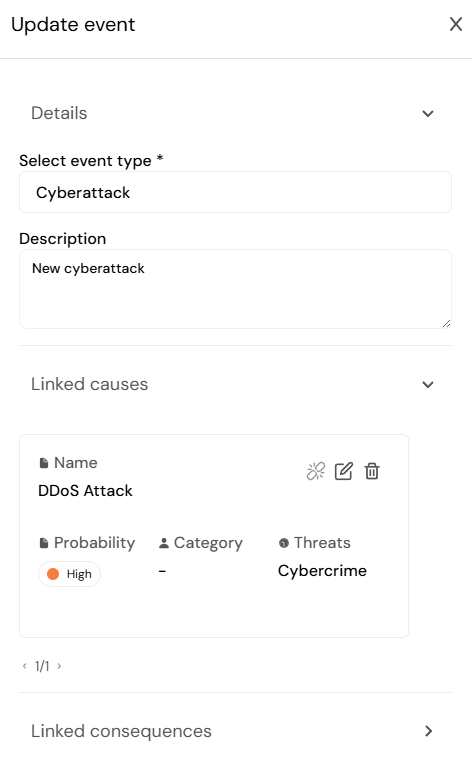
- Event: An occurrence or change of a particular set of circumstances. In Diri, the event is adverse and can have many causes and lead to many consequences.
- Event type: Predefined information securitys events to choose from. You can add a new event to the list if it is not present.
- Description: You can choose to add an extra description of the event, this text will be visible below the event title in the
¶ Consequence
- Consequence: Outcome of an event that affects objectives. The impact (outcome) from the event affects one or more assets.
- Consequence type: Similar to Event type, Diri contains a catalogue of known information security consequences to choose from. You can add a new consequence to the list if it is not present.
- Name: You can choose to further name your consequence.
- Add affected asset: Lets you choose assets from Step 2 - Asset evalutaion and include them in the impact analysis.
- Select implicated asset from the asset evaluation
- CIA: Choose if the consequence violates confidentiality, integrity, or availability.
- Assessment: Displays your asset evaluation of the selected asset within the chosen CIA category. Use this information as a guideline in the Consequence estimate.
- Consequence estimate: What is the inherent consequence level if the event materializes into this specific consequence without considering existing controls? Both existing and new mitigating controls are added later.
- Cost estimates: You can add cost estimates to the consequence to quantify the risk. If a consequence occurs:
- What will be the most likely minimum cost?
- What is the maximum it will cost?
- What is the expected cost (average)?
¶ Risk treatments
The risk treatment option can be found in the worksurface, after adding a cause or consequence: The option for adding new or existing treatment appears to the side of the card when hovering the mouse pointer over it:
The three choices for risk treatment are:
- New Treatment creates a new security control.
- Add existing allows you to re-use an existing treatment, meaning that an existing control will be used in your assessment. For global controls.
- Risk Treatment definition and options: Treating risk is a process to modify risk. The primary approaches to risk treatment are:
- Reduce the probability of event occurrence.
- Reduce the consequence of the the event impact.
- Avoid risk by removing the risk source.
- Sharing the risk (transferring) with another party or parties, through contracts and risk financing.
- Accepting the risk through informed choice.
¶ Registering a new treatment
- When clicking "New treatment" the following choices appear
- Name of treatment
- Description
- Type: Treatment types are categorised within the following three categories in Diri
- Physical controls are barriers in the physical domain, such as door locks, card readers, and fences.
- Technical controls are the technical barriers typically associated with cybersecurity, such as firewalls, network monitoring, and encryption.
- Administrative controls are security policies, guidelines, and routines, but also organisational security measures.
- Personell controls
- Class: A treatment class in Diri is derived from established security frameworks. The broad categorisation is as follows:
- Identify is a treatment class for developing the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect and maintain is a class for safeguarding and maintaining delivery of critical infrastructure services and asset protection (primarily probability
- Detect are treatmens for identifying the occurrence of a cybersecurity event.
- Respond and recover are treatments for developing and implementing the appropriate activities to take action regarding a detected cybersecurity incident. And for developing and maintaining plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
- Documentation link: Add a link to relevant documentation for the treatment
- Responsible user: Link the responsible user to the treatment. The user should be listed in the Diri user database for the quality function of following up the treatment to work.
- Due time: Select a deadline for the treatment. If selected, the responsible user will receive notifications of assigned treatment and deadline closing in.
- Cost estimations are used to calculate the total cost of treatment plan and high quality cost estimates are very useful in the cost-benefit analysis in step 4.
- Onetime Cost: What is the estimated one-time cost of the treatment? E.g. buying and implementing the treatment
- Yearly Cost: What are the estimated yearly costs of license and maintenance?
- Treatment effect: Is an estimate of relative control strength considering the cause or consequence. This estimate is subjective, but consider the threat agent in question and their capabilities when compared to the control effect. For example, multifactor authentication will generally be a strong control against several foreign adversaries.
- A note on treatment re-use: In the current version of Diri you can re-use treatments on multiple causes and consequences, but the treatment only has one effect estimate. Changing the treatment effect will impact all associated risks.
- Treatment Status displays the current state for the treatment, a treatment can be
- Open meaning that it has been identified and added as a suggestion to the risk.
- Recommended as a treatment for the risk but not planned.
- Planned the decision has been made to implement the treatment, but not yet started.
- Ongoing the treatment is currently under implementation.
- Implemented the treatment is completed and currently in use.
- The Treatment status and effect is used to calculate the risk picture in Diri:
- Before treatments describes the risk picture without any measures at all.
- Current risk describes the risk picture with implemented treatments in place.
- Planned risk describes the risk picture with implemented, planned, and ongoing treatments.
- All treatments describes the risk picture if all suggested treatments where implemented.
¶ Global and system-specific controls
One of the most complex issues in a risk management system is the many-to-many relationships between risk assessment objects (IT systems, vendors, assets, etc) and security controls. It is not uncommon that a control (treatment) has implications for the risk of many IT systems. Managing this is an essential issue as it prevents the same treatment from being registered and recommended multiple times.
We call it a global control when a unique control is included in more than one assessment. Typical global control mechanisms are single sign-on solutions that provide access to many systems and network firewalls that protect multiple systems and servers. A system-specific control only applies to one specific IT system.
System-specific treatments can also be made global by including them in new risk assessments. The treatment lists how many risk assessments it is included in and the number of risks it mitigates. A premise for re-using existing treatments is that the user has access rights to the treatment.
¶ Re-using existing treatments
Re-use is an excellent opportunity to save time in your DRA. The "Existing"-button lets you add existing treatments available to your user to risk asessment. Clicking this button lets you access and add from the treatments list. You can only re-use data from risk assessments that your user has access to.
If you wish to add an existing treatment, click the "Existing"-button besides the "New"-button. This action will show you a list containing the existing treatments from both the current risk assessment and other objects that you have access to. You can sort the list on all the available variables using managed tables, illustrated below.
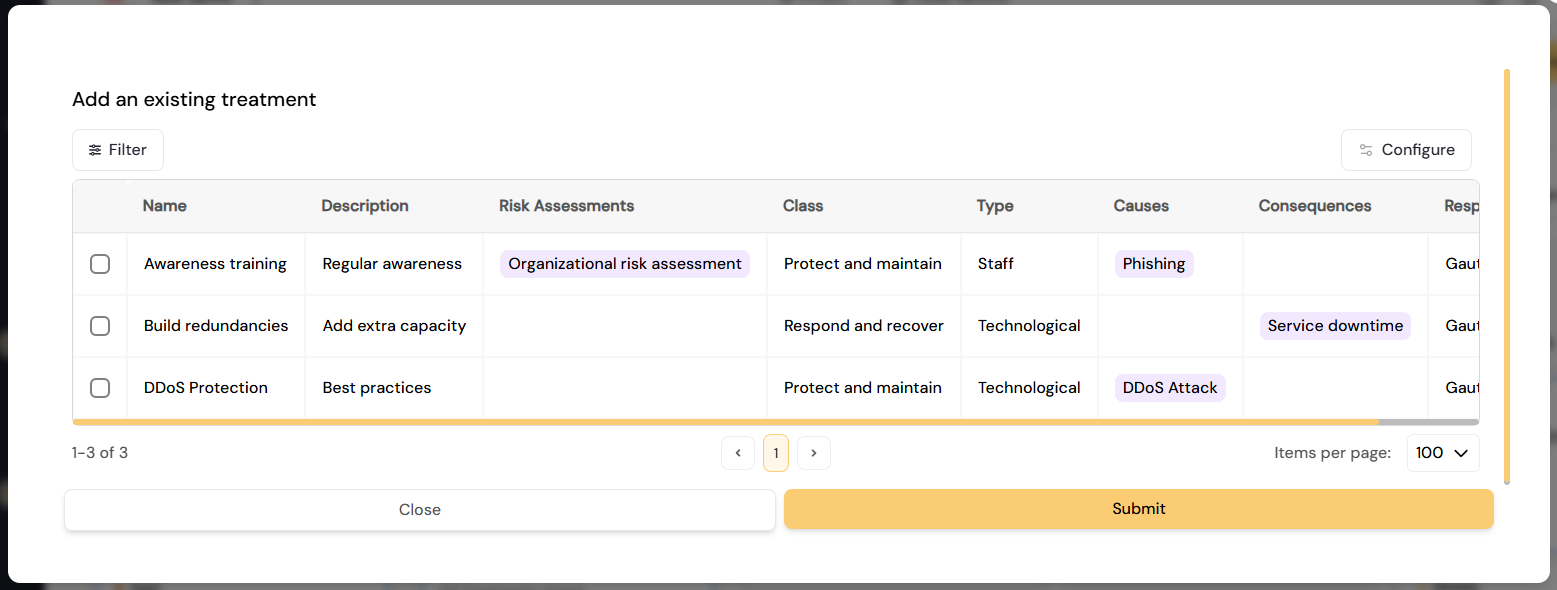
Important on re-use:
You can edit the content of existing treatments included in your risk assessments. However, there are separate treatment effects for each cause and consequence a treatment is added to. The illustration below shows the treatments list with the top treatment being used in two risk assessments and linked to two different causes with individual effects.
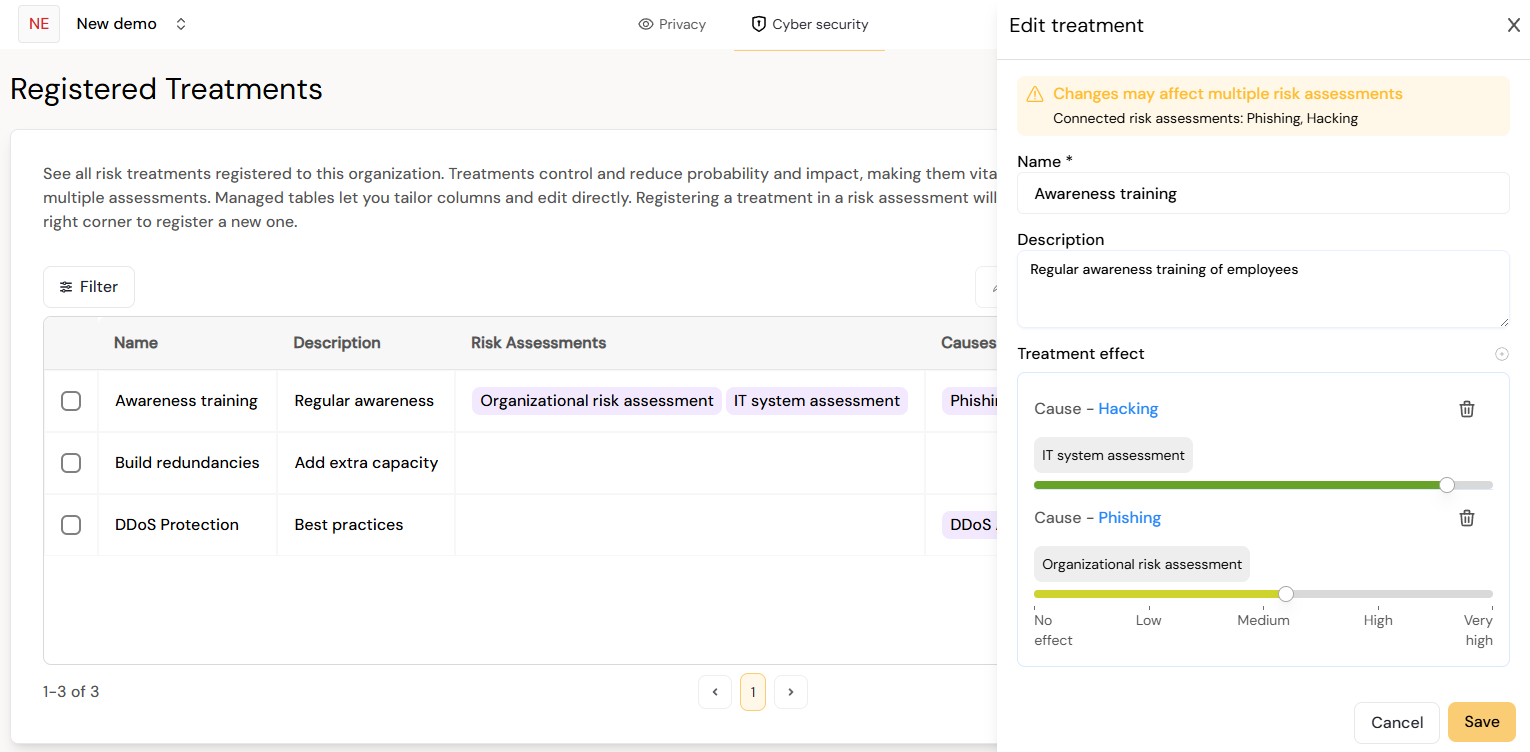
Opening the treatment card itself will show a warning that the treatment is connected to multiple risk assessments, and show as many individual treatment effects as there are connected causes and consequences.
¶ Risk estimations and calculations
Risk estimations in Diri:
- Everything in Diri is built on scales from 0-100, including choices in probability and consequences being sorted on the same scale.
- The control effect is also estimated on a scale from 0-100, but we can have multiple treatments for controlling one cause or consequence.
- Calculations of current risk in Diri is found using multiplication of inherent risk and implemented controls: (Inherent risk) * ((100-"control effect 1") /100) * ((100-"Control effect ...n")) /100) = Current risk example calculation:
A likely risk, p=80%, is mitigated by two implemented controls with moderate effects, C1=20% and C2=30%. In Diri the calculations are made as follows:
Current risk = 80 * ((100-20)/100) * ((100-30)/100)
= 80*0,8*0,7
= 44,8
The updated risk estimate will be placed on scale and categorized within the probability/consequence scale.