¶ Asset, Threat, and Vulnerability (ATV) Assessments in Diri
The Asset, Threat, and Vulnerability Assessment is the second step in Diri’s risk assessment process, and a crucial part of the risk identification phase as defined in ISO/IEC 27005. Asset, threats, and vulnerabilities must be added to the step 2 before they can be used in the risk assessment.
In this step, you identify and describe what needs protection (assets), what could cause harm (threats), and what weaknesses might be exploited (vulnerabilities). Together, these elements form the foundation for understanding potential risks to your organization’s information, operations, and compliance posture.
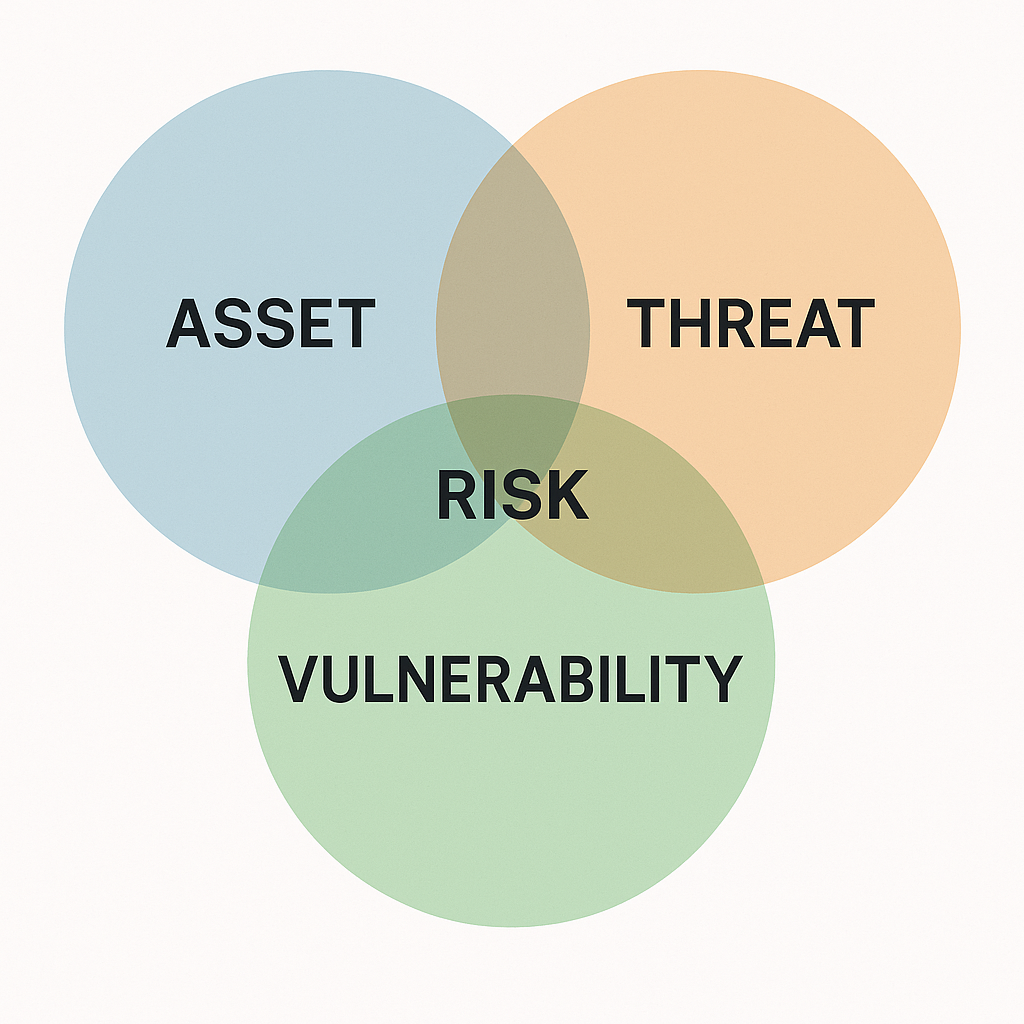
Diri provides structured tools to help you define, categorize, and assess these components efficiently. By maintaining a clear overview of assets, associated threats, and vulnerabilities, you set the stage for accurate risk evaluation and effective treatment planning in the next phases of the process.
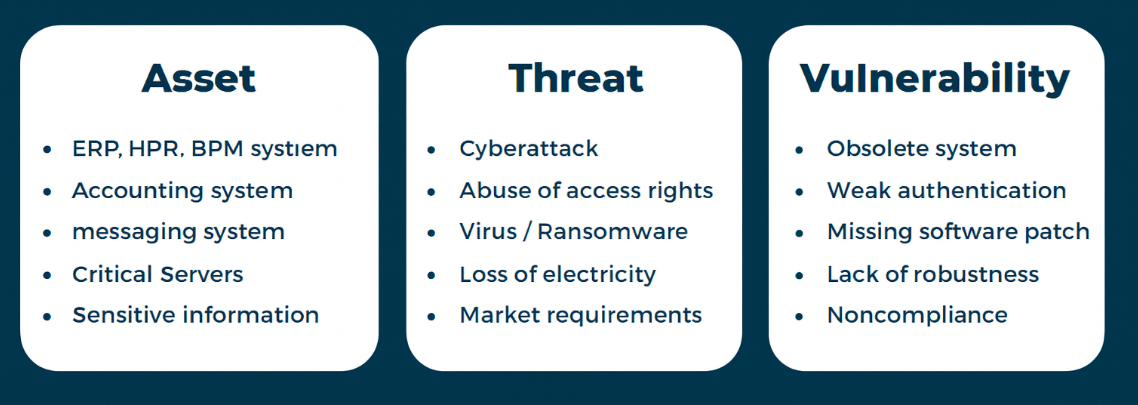
In Diri, the findings from the ATV assessment is plugged into the bowtie risk assessment as guidance for estimating probability and consequence, e.g.: What is the probability of threat X successfully exploiting vulnerability y causing the unwanted event? What will be the impact for the asset if consequences occur?
¶ Asset evaluation
Asset evaluation is the cornerstone of the risk assessment as it helps determine which assets need protection. An asset has value for the organization and must be protected. The main purpose of asset evaluation is to identify and prioritize critical assets and assess their need for protection. In Diri, this process is guided by structured asset categories and workflows designed to simplify the assessment while maintaining quality.
Conducting a proper asset evaluation provides several key benefits:
- Gain a clear overview of where critical assets are located in your organization.
- Establish a foundation for understanding risk — what happens if an asset becomes known, altered, or unavailable?
- Determine system criticality and define security or continuity requirements.
- Use assets as the basis for consequence evaluation in the Diri Risk Analysis (Step 3).
Start the asset evaluation by clicking on step 2 in the risk assessment dashboard. Clicking on the Add asset button will open the form for asset evalution, which looks like this:
¶ Information assets (Cybersecurity module)
For information security risk, our concern is primarily on information assets. Diri presents a novel process for mapping information assets that are either stored, processed, or transmitted in the risk-assessed object. In Diri, this object will often be an IT system. Step 2 aims to identify which information assets the system handles and prioritize them. Diri proposes to use an information classification approach for evaluating assets. This approach builds on the pillars of information security and evaluates the need for:
- Confidentiality - How secret is this information?
- Integrity - How dependent are we on that the data is correct, complete, and up-to-date?
- Availability - How long can we manage without the information?
Confidentiality, integrity, and availability, abbreviated as CIA. The information classification provides a way of understanding consequences if something happens to an information asset or system. We, therefore, use the classification results as a measure of system criticality and prioritizing.
¶ Information classification levels
In preparation for the asset evaluation, you should make sure that the information classification levels are defined with descriptions of each classification level. For assessment of CIA for values, Diri has developed four security levels as suggestions with descriptions that you can use. When we set the security level of the system, we use the highest ranked value, for example, if a system contains assets that are classified on level 4, then the security level of the system also becomes level 4. Asset evaluation is the cornerstone of information security because it determines how we approach the rest of the risk assessment according to the criticality level of the system. An object managing strictly confidential information will naturally have higher security requirements than one managing open information but be sure to consider requirements to integrity and availability.
Configure your classification levels in Settings, located under the General tab, select the "Levels for information classification and asset evaluation." You can configure how many classification levels you want in this setting and name the levels according to your existing policy.
¶ Business assets (Operational risk module)
For operational risk, our concern extends beyond information to include business assets — the people, processes, services, and physical or organizational components that enable the organization to function effectively. Diri provides a structured process for identifying and mapping these business assets within the risk-assessed object. In many cases, this object may be a business process, service, or organizational unit.
Step 2 aims to determine which business assets are involved and assess their importance to organizational operations. Diri proposes to evaluate business assets based on their contribution to overall operational resilience and continuity, focusing on the Criticality dimension– How essential is this asset for achieving business objectives?
The results provide a foundation for prioritizing risks and determining where mitigation measures will have the greatest effect on business continuity and resilience.
¶ Custom Business asset types
The business assets types are custom and set in Settings → Operational risk → Asset types. In this menu you can add and customize asset types for your organization. These are chosen as types in the asset evaluation form.
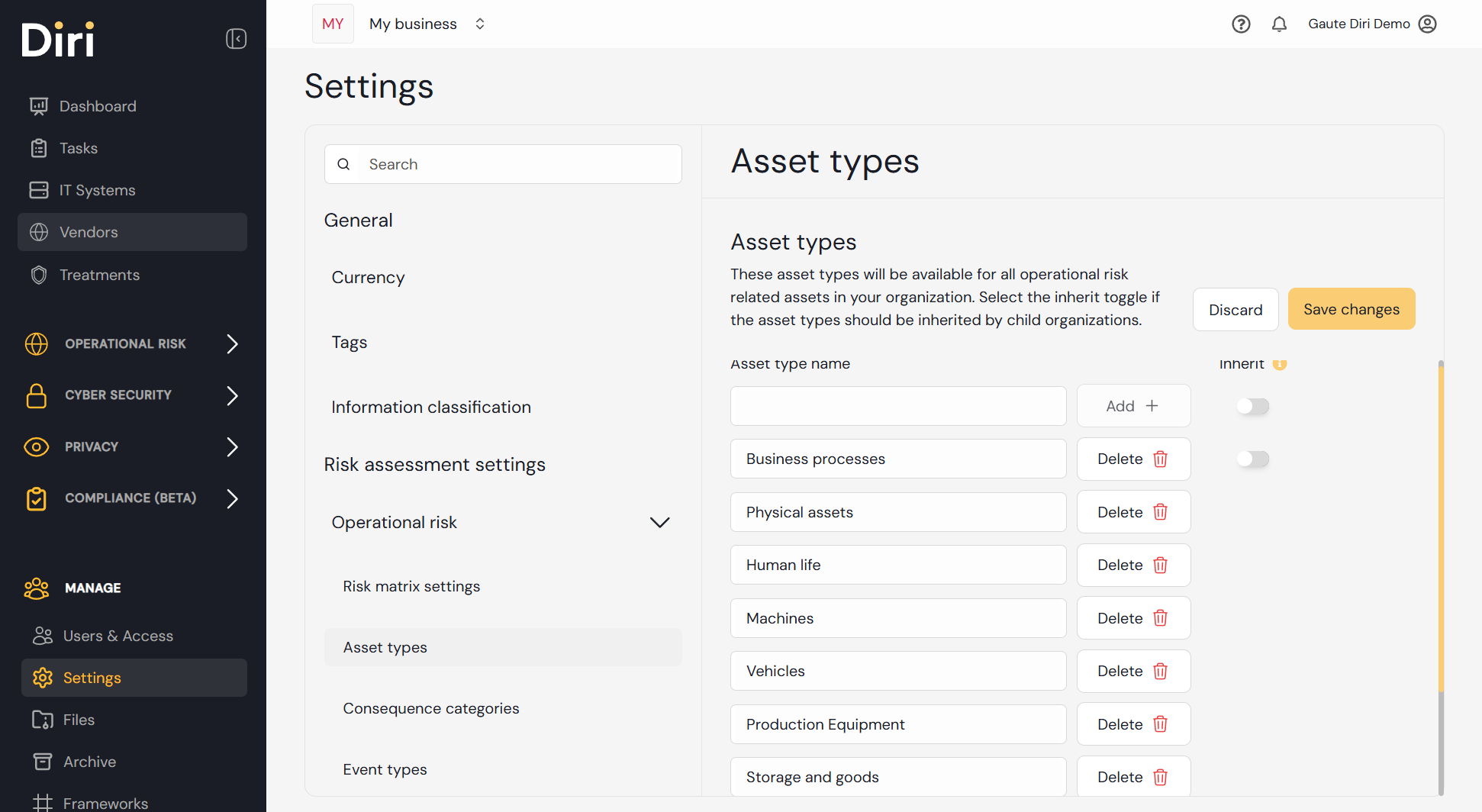
¶ Outcome of the asset evaluation
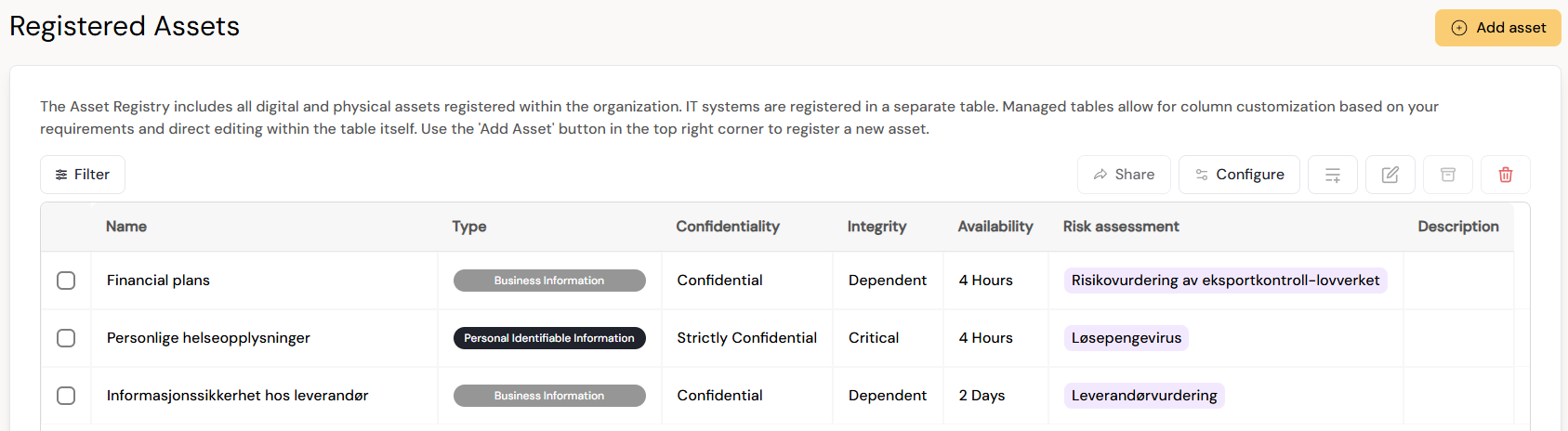
The asset evaluation results in a clear overview of your organization’s critical assets and their Confidentiality, Integrity, and Availability (CIA) classifications. This provides a structured understanding of each asset’s importance and the potential impact if it is compromised or becomes unavailable.
The identified assets are automatically included in Diri’s central asset register and become the foundation for the subsequent risk assessment, where they are used to evaluate threats, vulnerabilities, and consequences.
¶ Threat assessment
The Threat Assessment in Diri helps you identify and describe potential sources of harm that could affect your organization’s assets, operations, or information. It is a key part of the risk identification process and supports later analysis and treatment planning.
In this step, you add and describe each threat, then assign a threat level to indicate its potential impact. Diri provides structured guidance and examples to help you consider both internal and external threat sources — such as human error, technical failure, malicious activity, or natural events.
When a threat is created, it is automatically added to Diri’s central threat register, making it available for reuse in other risk assessments. Threats linked to a specific assessment can also be used directly in Bowtie risk analysis, helping visualize causes, consequences, and existing controls.
The purpose of the Threat Assessment is to build a consistent, organization-wide understanding of what could cause harm and how severe the impact could be — forming the basis for effective risk evaluation and mitigation.
¶ Vulnerability Assessment
The Vulnerability Assessment in Diri helps you identify weaknesses or conditions that could make your assets more susceptible to threats. It is an essential part of the risk identification phase and directly supports both threat and asset evaluations.
In this step, you add and describe each vulnerability and assign an exposure level to indicate how easily the weakness could be exploited. Diri provides guidance and examples to help you consider different types of vulnerabilities — such as technical flaws, missing controls, human factors, or organizational gaps.
When a vulnerability is created, it is automatically added to Diri’s central vulnerability register, making it available for reuse in future risk assessments. Vulnerabilities linked to a specific assessment can also be used in Bowtie risk analyses to visualize their role in enabling threats and identify effective barriers or mitigations.
The purpose of the Vulnerability Assessment is to build a clear picture of your organization’s exposure — showing where weaknesses exist and how they might contribute to risk. This insight provides a strong foundation for prioritizing improvements and reducing overall risk.
¶ Summary
In Diri, Step 2 of the risk assessment process focuses on identifying and understanding assets, threats, and vulnerabilities — the core components of risk as defined in ISO/IEC 27005.
You begin by evaluating assets, both business and information-related, to determine what is critical and how it should be protected. Each asset is classified according to Confidentiality, Integrity, and Availability (CIA), forming the basis for consequence evaluation.
Next, you assess threats — potential sources of harm — by describing them and assigning a severity level. Finally, you identify vulnerabilities, or weaknesses that could be exploited, and rate their exposure level.
Each element added in this step is automatically stored in Diri’s central registers (assets, threats, and vulnerabilities) for reuse across assessments. Together, these assessments create a structured foundation for understanding risk and support advanced analysis, including Bowtie visualizations in later steps.