¶ The Relationship Between Vendors, IT Systems, and Information Assets
When managing information security and privacy, it's important to understand how vendors, IT systems, and information assets are connected. These three elements form the foundation of your organization's digital ecosystem—and securing them is essential. This relationship shapes the context of your digital security management.
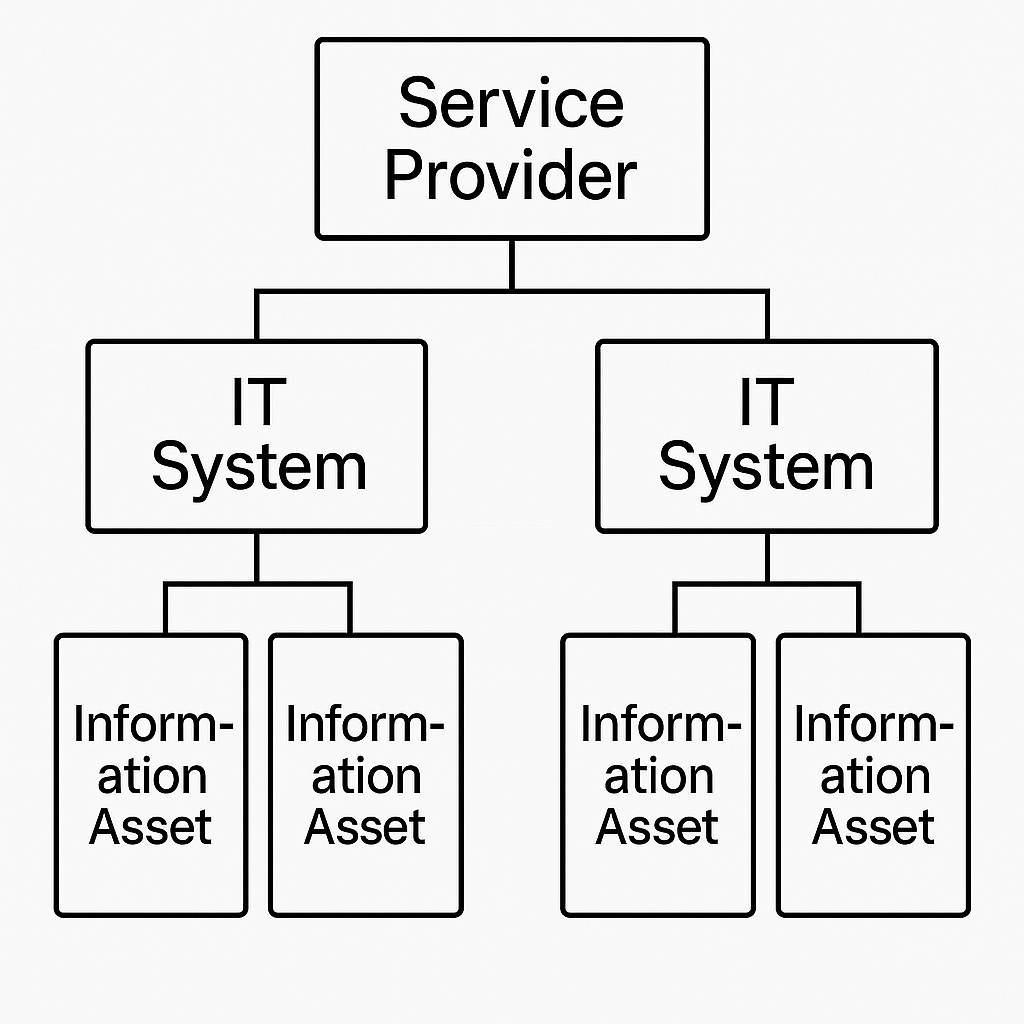
Security risk assessments can consider IT system, but also who provides it (vendor) and what it holds (information asset).
Privacy compliance (like GDPR) often requires mapping which vendors process personal data, on which systems, and for what purpose.
Access control, incident response, and data protection measures must be aligned across all three.
¶ 1. Vendors
The Vendor Registry in Diri helps your organization keep track of all external vendors and service providers that may impact your information security or privacy compliance. Vendors are external parties who provide services, software, infrastructure, or support. This can include:
- Cloud service providers (e.g., AWS, Microsoft 365)
- Software vendors (e.g., CRM systems, accounting software)
- IT support companies or consultants
Why it matters: Vendors often have access to your systems or data, or process data on your behalf. Their security practices directly impact your organization’s risk.
¶ 2. IT Systems
The IT System Registry in Diri gives you a complete overview of the digital systems your organization uses—whether they're internal platforms, cloud services, or vendor-supplied tools. IT systems are the tools and platforms your organization uses to operate—many of which are delivered or maintained by vendors. Examples include:
- Email platforms
- CRM systems
- Business applications
Why it matters: These systems store, process, or transmit your organization’s information assets. Any vulnerabilities in these systems can expose data to unauthorized access or loss.
¶ 3. Information Assets
The Asset Register is a listing of all the assets that your users can see in the Diri application. The assets can be sorted according to location, risk assessment type, name, asset type, and criticality. And you can filter and search through your assets using the filtering function.
Information assets are the data and records that are valuable to your organization. These can include:
- Personal data (e.g., customer or employee information)
- Business-critical documents (e.g., contracts, financial records)
- System configurations or intellectual property
Why it matters: Protecting information assets is at the heart of both information security (confidentiality, integrity, availability) and privacy compliance (e.g., GDPR).
Information is ranked according to information classification standards:
- Confidentiality - How secret is this information?
- Integrity - How dependent are we on that the data is correct, complete, and up-to-date?
- Availability - How long can we manage without the information?
The CIA levels are configured in the settings.