¶ Settings in Diri
Diri comes with several tailorable variables that you can adapt to fit your own security policies and guidelines. The Diri settings are dived into categories which are bound to modules. There are individual settings per module, e.g. the risk matrix setting can be different between the privacy, cybersecurity, and the operational risk modules.
- Many organizations already have pre-defined levels for probabilities and consequences, data classification, and revision times. These can be plotted under General settings.
- Type definitions relates the Diri libraries of vulnerabilities, consequences, threats, and events. These settings are connected the data aggregation and statistics.
Following best practices you should have a security policy or guideline supporting several of the general settings in Diri.
The settings option is found at the bottom of the main menu. Note: You will need to “save changes” in the end, or the changes will not be saved.
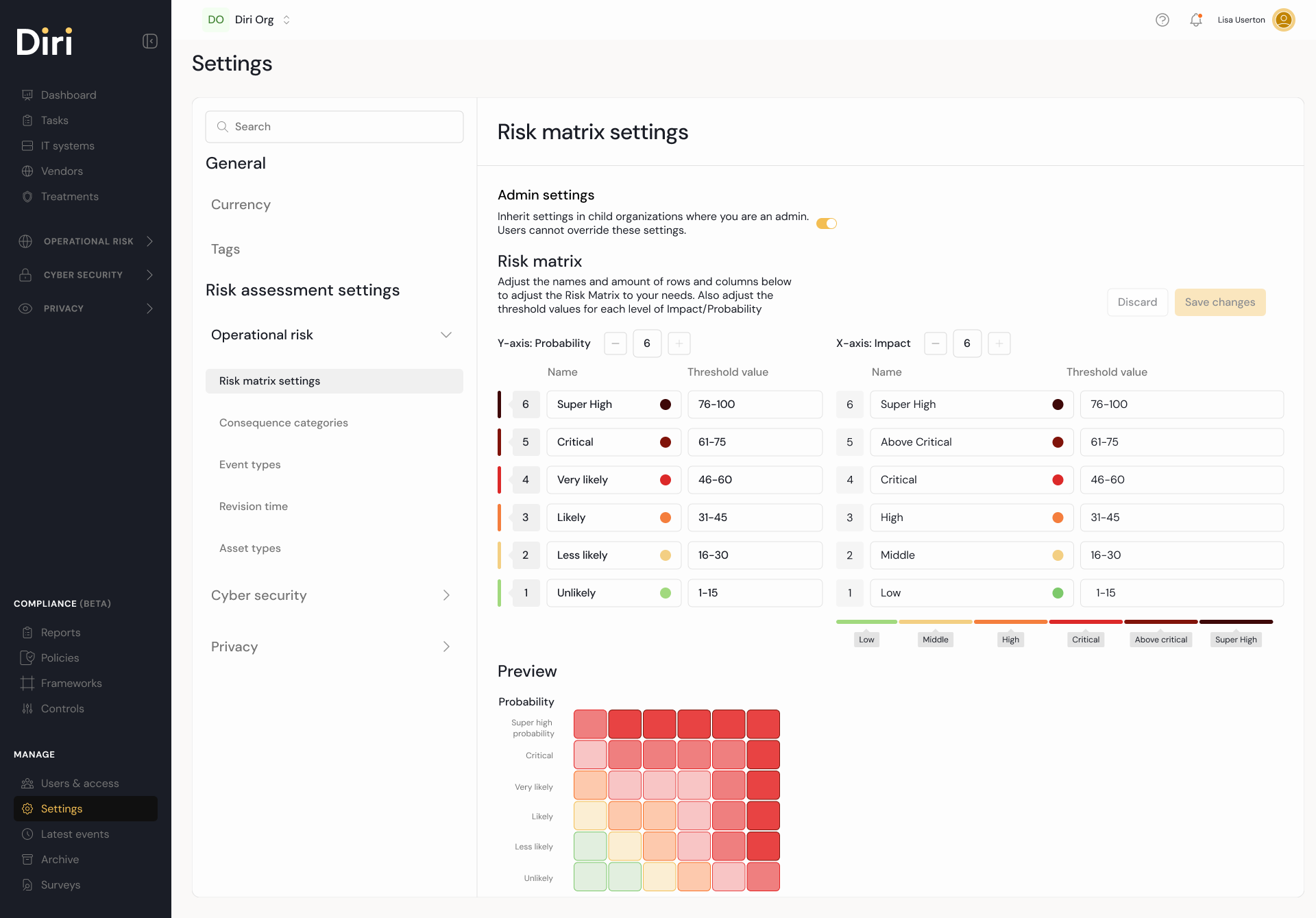
The above picture shows where to locate the settings, bottom left in the main menu, with modular settings. The picture shows settings for the risk matrix and customizable risk levels.
¶ Modules and selection
In Diri, features are organized into modules, making it easy to tailor the platform to your needs. Your subscription level determines which modules you have access to. Each module unlocks a set of features designed to support specific tasks—such as risk assessments, vendor management, or compliance reporting. If a feature is unavailable, it may be part of a module not included in your current subscription.
¶ General settings
¶ What does the settings do?
In summary, the settings are connected throughout the application and users encouter settings while doing tasks in Diri. The settings are used the following way:
- Risk matrix settings for probability and impact are used in the risk assessment:
- Probability settings determine the available levels for the users when assessing the probablity of a cause occurring.
- Impact settings determine the available levels for the users when assessing impact severity of a consequence occurring.
- Both are used to determine the Y-axis (probability) and X-axis (consequence) of the risk matrix
- Information classification levels are available when doing asset evaluation.
- Threats and vulnerabilities are determines the choices available for the user in the bowtie risk assessment cause.
- Event types are risk criteria for determining which category an event falls into, e.g. Unauthorized access, service disruption, compromised users, etc. The types are utilized in the event of the bowtie analysis.
- Consequence types are risk criteria for determining which category a consequence falls into, e.g. financial loss, availability, data loss, data breach, etc. The types are utilized in the consequence of the bowtie analysis.
- Revision time determines how long it should take from a risk assessment gets signed to it needs revision.
- Currency determines which currency type is shown throughout the application.
¶ The Risk Matrix
The probability and consequence levels are central in the risk assessment and reporting. These settings are applied when assessing risk and aggregating data into the dashboard.
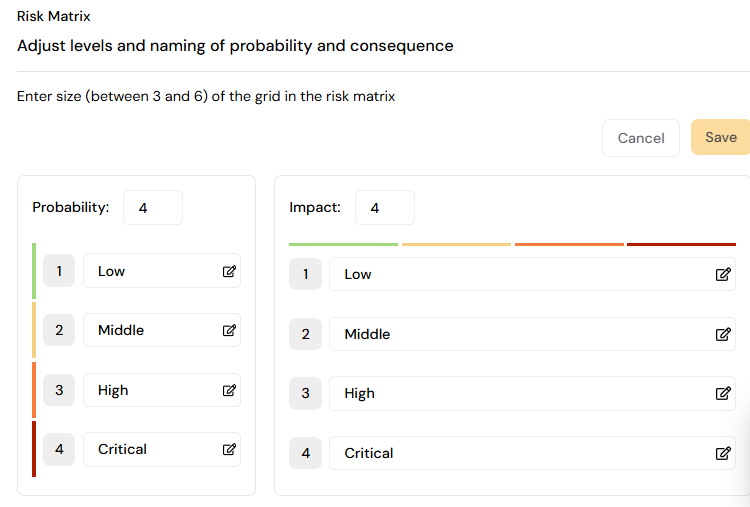
In Settings > Module> Risk matrix, it is possible to rename consequences and probabilities as well as how many different levels of these two you want to take into consideration. What is essential to keep in mind here is that the number of different levels you create must match the number at the top of the consequences and the probabilities. That number beside these categories is how many of the levels will appear as choices during the risk assessment. (Six levels is the current limitation of the levels, but let us know if you need additional levels.)
These settings are stored on the current organizational level and inherited downward in the organization. However, you can create tailored levels on lower organizational levels. The data still aggregates into the dashboard at higher levels without problems.
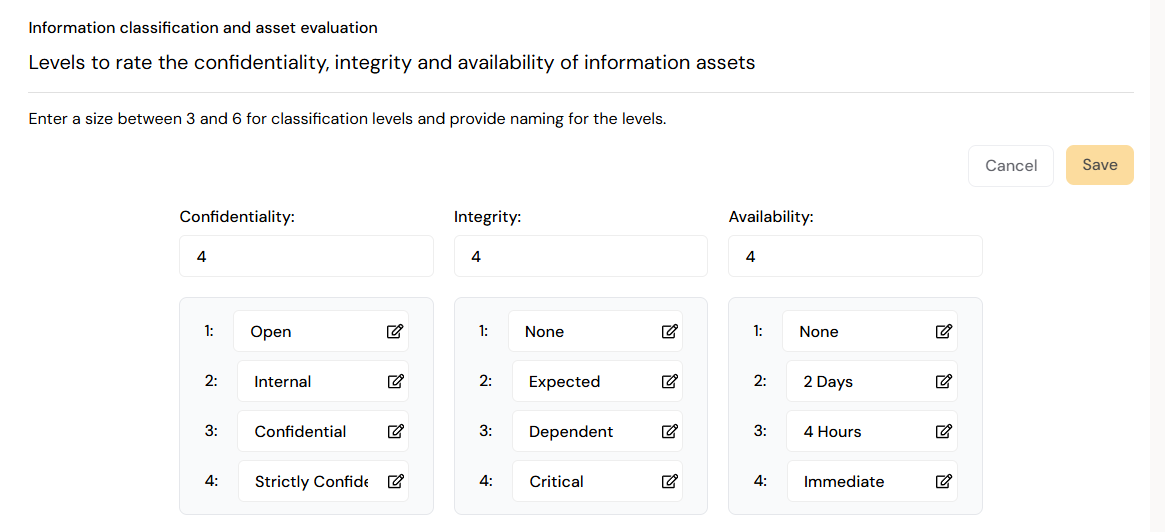
¶ Levels for information classification and asset evaluation
Asset evaluation is the cornerstone of the risk assessment as it helps determine which assets need protection. An asset has value for the organization and must be protected. Information classification is a central part of the asset evaluation
The classification levels are a direct input to your risk assessment consequence estimate and security management as a whole. Classifications are done within the so-called "CIA" levels; confidentiality, integrity, and availability. These levels should fit your organization's data classification policy.
It is also essential that the number of levels matches the number at the top so that everyone can be selected in the risk assessment. Remember to save changes; this is not done automatically.
¶ Currency
In the currency settings, it is currently only possible to change the currency. The currency is used to keep track of the costs in the treatment list and plan.
¶ Revision time
Revision Time defines how long the action plan is valid before it needs to be revised. For example, one can set a validity of 12 months for annual revision which tracks into your dashboard and sends notification to risk assessment owners.
¶ Type definitions (Libraries)
The type definitions are the options you have available in the risk assessments. Please note that you cannot delete any options that are currently in use in risk assessments. The "delete" option will be grey and non-clickable for these items.
¶ Vulnerabilities
You can add, edit, and remove vulnerabilities from your risk assessment. Diri comes with four predefined vulnerability domains (Human, Organisational, Physical, Technical), but you can add a higher granularity if you wish. These choices are linked to data aggregation and statistics in the Diri application.
¶ Threats
Under threats its possible to add or customize various threats such as Unfaithful employees, terror, criminals, natural disasters and so on.
¶ The Consequence Category and Event Category
You can add or customize different events that may occur based on causes and threats. Similarly for consequences if the threat event occurs. The Consequence and the Event Categories are a bit special because you can not add consequences and events directly in to the library, Consequences and Events are added to the library through the risk assessment step 3 (requires registered user). Events and Consequences are added by clicking "New" in the Risk assessment.